News - a Roundup of all the news items between April 2007 and May 2007, Newest First
 To avoid long load times news is archived periodically. If you can't find what you are looking for on this page please refer to our archives. Please use the search engine for ease of retrieval.
To avoid long load times news is archived periodically. If you can't find what you are looking for on this page please refer to our archives. Please use the search engine for ease of retrieval.
Main News page |
Archives: (oldest)
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13
(most recent)
Whistleblowing Hotline Guidelines for Germany
Unlike other countries in Europe (e.g. France), Germany does not have any official binding rules on the admissibility of Whistleblowing Hotlines. However, the Ad-hoc Working Group on "Employee Data Protection" of the Düsseldorfer Kreis ("Working Group") has recently issued a report on Whistleblowing Hotlines and data protection. Although the recommendations in this report have no binding character, they will materially influence the embodiment of Whistleblowing Hotlines, because the various data protection authorities in Germany normally adopt these recommendations.
The Working Group which exists of representatives of the data protection authorities of the private sector in Germany generally accepts the establishment of such Hotlines to report misconduct as an addition to internal management. For the application of the general legal principles on Whistleblowing Hotlines, the Working Group qualified the following groups as breaches of codes of conduct:
Read the article
Ponemon and Vontu Study Reveals that Data Breaches Undermine Consumer Confidence
Fear of Data Loss and Identity Theft Has Changed Consumers' Purchasing Behaviour
In the wake of massive data breaches at businesses, educational institutions and medical facilities, consumers are modifying their purchasing behavior, including online buying, out of concern for the security of their personal information. The 2007 Consumer Survey on Data Security from Vontu, the leader in Data Loss Prevention solutions, and the Ponemon Institute, a leading privacy and information management research firm, found that 62 percent of respondents have been notified that their confidential data has been lost.
The high percentage of individuals that have been notified of a data loss event has contributed to increased security concerns, as the vast majority of those notified reported concern about the event. These data breaches have had a direct impact on consumer buying behavior, including reluctance to use their credit or debit card to make a purchase with a Web merchant they don't know, and unwillingness to provide their Social Security number online.
"Our research clearly shows that data breaches are affecting consumers' trust in the organizations with which they share their data and, ultimately, their buying behavior,” said Dr. Larry Ponemon, chairman and founder, Ponemon Institute.
Read the article
Do SSL VPN checks measure up to the rigors of NAC?
Many SSL VPN vendors assess the security of endpoints as part of their network-admission routine, but that doesn’t mean these assessments are equivalent to NAC.
The purpose of SSL VPN endpoint checking and NAC are similar - to evaluate the security posture of the device and impose an access policy based on that evaluation.
Most SSL VPN vendors that do this use downloadable software agents to do the work, supplemented by a permanent SSL VPN client for managed machines that need network-layer VPN access.
read on in Network World
MIFID-EU executive to step up non-compliance legal action
BRUSSELS, June 26 - The European Commission will step up legal action against 24 European Union countries for being late to introduce sweeping new share trading rules into national law.
"We will step up the 24 legal actions tomorrow," an EU source said on Tuesday.
Only three EU states -- Britain, Ireland and Romania -- introduced the bloc's Markets in Financial Instruments Directive (MiFID) into national law by the Jan. 31 deadline.
Read the Reuters article and the Reuters update
Boutique Malware: Custom-Made for the Executive Suite
A malware spam scheme that started in early June surfaced as an apparent e-mail from the Better Business Bureau. The message appeared to be legitimate and differed from previous types of e-mail scams. For instance, the spammers sent the message on a much smaller scale in an attempt to fly under the radar of most service providers. It was sent primarily to executive-level company managers.
A sophisticated group of spammers has been targeting since late May high-salaried workers at selective corporations in a spam attack using e-mail disguised as messages from the Better Business Bureau (BBB), the Internal Revenue Service (IRS) and the Federal Trade Commission (FTC).
A fourth variation of the spam attack surfaced the second week of June as an e-mail invoice from a variety of companies seeking payment for services rendered.
"The Trojan is unusually capable. It sits in the compromised computer and captures specific types of sensitive personal data before it gets encrypted through the SSL socket. It gathers names, passwords, account numbers, etc.," Paul Henry, vice president for technology evangelism at Secure Computing, told TechNewsWorld.
The continuing attacks appear to be from the same group. The wording, data location and Trojan are the same. The only thing changed in each new appearance is the attack vector, according to several security experts who spoke with TechNewsWorld.
read the article at MacnewsWorld
Pornography sites are exposing visitors to the hack toolkit, Mpack
Several hundred pornography sites are surprising unwitting users with a smorgasbord of exploits via Mpack, the already notorious hacker toolkit that launched massive attacks earlier this week from a network of more than 10,000 compromised domains.
Trend Micro has spotted nearly 200 porn domains -- most dealing in incestuous content -- that have either been hacked or are purposefully redirecting users to servers hosting Mpack, a professional, Russian-made collection of exploits that comes complete with a management console.
Even though there are far fewer porn sites in this newly discovered infection chain than in Monday's "Italian Job" attack -- called that because most of the 10,000+ hijacked sites were legitimate Italian domains -- they've managed to infect twice as many end-users' PCs, said Trend Micro in a posting to its malware blog .
"Right now, we are not sure whether the porn sites are compromised to host the IFRAMES, are created to do so, or are being paid to host the IFRAMES," acknowledged Trend Micro. The attack probably began June 17, the company said.
Read on at ComputerWorld (the article is office friendly)
Carefully crafted security attacks confirm the development of a malicious economy
F-Secure's Data Security Wrap-up for the first six months of 2007 looks at the top security threats witnessed by the anti-virus provider from January to June of this year. During this period, the F-Secure Lab saw a steady flow of reports on a vast variety of data security threats.
The underlying trend to note was the spread of malicious activity across various forms of technology and applications during the six-month period. It would appear that the parties behind orchestrating security attacks are conquering more and more foothold to build a stronger, sustainable commercial economy based on carefully crafted security attacks targeting consumers, companies and public sector organisations.
Social engineering progressed to a new level of sophistication via the Small.DAM Trojan, causing havoc via e-mail in January, 2007. Masking itself under the pretence of shocking headline news, linked to real-life events such as the January storms in Europe, the Storm-Worm spread at an alarming speed across the globe in just one night.
Read more at Security Park
ID 'visher' called home
One of the biggest challenges for consumers is to keep informed about the latest scams. ID thieves, for instance, are constantly changing their tactics in efforts to take advantage of consumers like this New York City man.
"I recently received a voice message from my bank. The representative told me he had my first name, but said he needed me to call back and verify several pieces of information, including my last name and account number. I refused. I called the number, because I wanted to explain my position. But I just got a bunch of automated prompts. There was no one to talk to, so I hung up," he explained. "Is there any way to find out anything more about this?"
You did the right thing by hanging up. By refusing to give any personal information, you prevented yourself from becoming a vishing - or voice-phishing - victim.
Read more on NY Daily News
Phishing on the rise as bots decrease
New research finds that phishing attacks have increased by nearly 800 per cent in the three months of this year.
Phishing attacks have risen over the last six months while use of botnets appears to have slowed down, according to latest research.
The findings from anti-virus company McAfee update predictions made earlier in the year. McAfee's research team Avert Labs saw a 784 percent increase in phishing websites in the first quarter of 2007 and it said there was "no slowdown in sight".
The team said that it anticipated increasing abuse of sites meant for online collaboration such as wiki pages and online applications. Even internet archive sites will suffer, according to the researchers.
read more on ITPRO
UK sets the pace when it comes to cyber crime
Identity theft, phishing and Trojan attacks are on the rise, and virtual worlds are being targeted by fraudsters, said a global online security firm.
UK is a popular target because it was the pioneer for fast online payments, and consumers are used to easy and instant payment transfers, said Uriel Maimon, senior research scientist, RSA consumer solutions.
Financial firms continue to face new and emerging threats, and are challenges to increase confidence in the online medium, mitigate against risk and keep fraud loss low.
New scams are also emerging in virtual worlds, such as Second Life, according to Maimon. He said there are two common ways that attackers are targeting virtual worlds. Firstly, end users tend to use the same password for their virtual world as they do for their online bank account, so attackers try to uncover this through phishing attacks.
Read more at TechWorld
Google releases API to help with online fight against cybercrime
If you use Google Desktop, or Firefox 2.0, then you are likely used to the warnings you might come across if you visit a potential malicious website. One of the things that make the website blocker and warning system work is an API (Application Programming Interface) that calls on a Google created and maintained black list of URLs. The black list is all of the known sites that are related to reports of Phishing, Malware hosting, and other online crimes. The list is updated constantly, and with the help of the newly released API, developers can start using Google's list for other creations.
Phishing and Malware are a serious issue online. The list created by Google comes from several sources including information sent to the teams by normal internet users. The lists are used to deny access to sires that spread Malware, or are used in cases of fraud online. Developers wishing to use the API, can signup for the code as well as an API key. While there are some rules, mostly the program is well received by security experts and developers alike.
read the article at monstersandcritics.com
Cyber Criminals Rely On Mind Games To Scam Internet Users
McAfee Study Offers Insight into Psychological Tactics Used in Online Scams
McAfee, Inc. (NYSE: MFE) today (25 June 2007) announced the results of a groundbreaking study that details the psychological games and other tactics cyber criminals use in social engineering scams propagated through junk email. In the study titled "Mind Games," the primary author, Dr. James Blascovich, Professor of Psychology at the University of California, Santa Barbara, offers analyses of multiple common scam emails and provides surprising insights into how cyber criminals use fear, greed and lust to methodically steal personal and proprietary financial information.
The same psychological practices used by cyber criminals were also investigated in a European report, commissioned by McAfee(R) in association with leading forensic psychologist, Professor Clive Hollin, based at University of Leicester in the United Kingdom.
"Scam spam works best by providing recipients with a sense of familiarity and legitimacy, either by creating the illusion that the email is from a friend or colleague, or providing plausible warnings from a respected institution," Dr. Blascovich noted. "Once the victim opens the email, criminals use two basic motivational processes, approach and avoidance, or a combination of the two, to persuade victims to click on dangerous links, provide personal information, or download risky files. By scamming $20 from just half of one percent of the U.S. population, cyber criminals can earn $15 million each day and nearly $5.5 billion in a year, a powerful attraction for skillful scam artists."
Read the article
UK extends ecommerce directive to terrorism laws
Regulations come into force this week that explain how and when a foreign company can be brought to justice in the UK over blog postings that encourage terrorism. The regulations integrate Europe's ecommerce laws with the UK's Terrorism Act.
The Electronic Commerce Directive (Terrorism Act 2006) Regulations 2007 were laid before Parliament on 31 May and come into force on 21 June.
The Terrorism Act 2006 is already in force. It created offences relating to the encouragement of acts of terrorism and the dissemination of terrorist publications. The Act contains a notice and takedown regime that applies to all website operators. If a person posts any remark to a blog that encourages an act of terrorism, a police constable can serve a notice on the operator of the blog requiring the removal of the offending post within two days.
Failure to comply within the two-day period, in the absence of "reasonable excuse", means the operator will be deemed to have endorsed the post and its directors could face up to seven years in prison.
Read more in The Register
Technology stalls take-up of algorithms
Fund managers in Europe have been slow to embrace algorithmic trading compared with their US counterparts. Poor technology has been blamed and, while the markets in financial instruments directive may eventually encourage algorithmic trading, fund managers' time and resources are focused on other projects.
Algorithms make up 12% of trading volume at asset managers using the systems in Europe (see chart) and the share has nearly doubled in the past year. Some fund managers and technology providers say use of this advanced electronic trading tool will accelerate.
Michael Holman, head of global trading at Axa Rosenberg Investment Management, said: “The take-up in Europe has been fairly rapid in the past six to nine months. There's a lot of pressure on fund managers to change because of the increasing concentration on (execution) cost savings.” He expects algorithmic trading to reach 28% to 35% of total trading volumes in Europe.
Read more in Financial News Online
Financial services CIOs reveal investment priorities
One-fifth of this year's CIO50 list is represented by the financial services sector. With the industry still dominated by pressure to keep costs down and with little growth in tech budgets forecast for the next three years, Andy McCue talks to two financial services CIOs about current investment priorities and future trends...
Financial services has traditionally been, and still very much is, the industry that spends the most on technology, both pound for pound overall and in terms of the percentage of company revenues set aside for the IT budget.
The current figures are truly eye-watering. In UK retail banking alone - just one segment of the massive financial services vertical - IT spend is tipped to reach almost £10bn this year, according to analyst Gartner's latest forecasts. In securities that figure is £6.6bn while in insurance the total is £5bn.
But despite the huge headline figures the underlying trend is still one of caution when it comes to IT investment. Gartner is only predicting compound annual growth of around five per cent in financial services IT budgets through to 2010.
Read the Silicon.com article
Alternative trading systems in Europe face post-MiFID hurdles, says Celent
Alternative trading systems in Europe will struggle to increase trading volumes, despite catalysts such as MiFID, according to Celent, a Boston-based financial research and consulting firm. The most likely scenario, in the near term, is that equity execution options will increase, but little liquidity will be siphoned away from the traditional exchanges.
Celent estimates that in the UK, ATSs have attracted less than 0.5% of the equities market, and that in Germany this number is lower still, essentially close to 0%. In France, Italy, and Spain, with concentration rules severely limiting off-exchange trading, the volume of equities trading in ATSs is, not surprisingly, about 0%.
By 2011, Celent predicts that ATSs in Europe will have captured only 5% market share. Off-exchange equities account for a sizable 11% of total transactions in Europe. The on-exchange equities market is of course significantly larger at 54% of total European transactions.
Read the Tekrati article
MiFID – best execution still a concern – and the Boat sails on
Best execution requirements under the EU's Markets in Financial Instruments Directive (MiFID) remain the "biggest piece of work" in firms' MiFID projects according to the MiFID mid-tier special interest group, the Financial Services Discussion Club , at their monthly meeting in London on June 4th.
The conditions stipulated under best execution were seen as the main challenge for firms, as members detailed the issues in putting appropriate policies together. There was particular concern about synchronising best execution policies between buy-side and sell-side firms. Many buy-side firms were waiting on information from sell-side counterparts in order to put best execution policies together and were concerned at the diminishing time-frame available to them before November this year to complete this part of the project. Traders' increased responsibility to document that best execution policies have been followed was also seen as a taxing issue.
Read the Chase Cooper article
Jail sentences for data protection fraudsters
The Information Commissioner’s Office is again reminding businesses across the UK not to be misled by bogus agencies that send notices demanding money to register under the Data Protection Act 1998 (DPA).
The warning comes after Leeds Crown Court sentenced three men to prison on Friday 8 June for their involvement in fake data protection agencies. Bogus letters were sent to thousands of businesses demanding registration fees of £135 to
register under the DPA in a mail scam which could have potentially netted up to £2 million for the fraudsters.
Neil Clark, prosecuting for the Crown, explained to the Court that £62,575 had already been banked by the fraudsters but the police had also found that thousands of printed bogus forms were ready to be posted to unsuspecting companies when they ended the operation. Liaquat Khan, aged 33 of Leeds, admitted two charges of conspiracy to defraud and was jailed for two and a half years. Parminder Kaur Johal, aged 31, and Zahir Abbas Shah, aged 33, both from Bradford, also admitted two charges of conspiracy to defraud and were jailed for 13 months and 8 months respectively. A fourth person, Nosheen Sheridan, aged 27 from Bradford, admitted one charge of conspiracy and was given an 18 month supervision order with 50 hours unpaid work. On passing sentence, Judge Roger Ibbotson said that they were involved in a substantial and systematic fraud. He commented: “You specifically targeted the owners of small businesses” and relied “on their wish to act lawfully and not commit any breach of the regulations”.
Read the article
Privacy: Do online shoppers care?
Would you pay a little more for that book you bought online if it meant lowering your chances of being hassled by marketers, spammers and hackers?
Researchers at Carnegie Mellon University believe consumers will pay more per item online to protect their private information, according to a paper presented at the 2007 Workshop on the Economics of Information Security.
The Carnegie Mellon Usable Privacy and Security Lab (Cups) monitored the habits of people ranging in age from 18 to 71 who were given money and instructed to buy certain items online while using the search engine PrivacyFinder.org.
PrivacyFinder.org, a search engine developed by Cups, evaluates a website's privacy policies according to the Platform for Privacy Preferences developed by the World Wide Web Consortium. It displays a site's rank alongside search results.
Read more on Silicon.com
Nearly 40 Percent of Large Organizations Don't Monitor Databases for Suspicious Activity – Or Don't Know If They Do. [Ponemon Institute]
Customer and employee data remains at greatest risk; IT understands the threat, but competing corporate priorities fuel epidemic of data theft and misuse
Application Security, Inc., today (4 June 2007) announced the results of a Ponemon Institute survey that underscores the serious challenges large organizations face in securing sensitive data. With more than 150 million data records exposed in just the past two years, the survey also highlights an organizational disconnect between the realization of the threat and the urgency in addressing it.
Conducted by one of the world's foremost authorities on data security and privacy, the Ponemon Institute survey queried 649 respondents in corporate information technology (IT) departments within U.S.-, European- and Middle Eastern-based business and or government organizations. Respondents averaged more than 7 years of experience in the information security field; more than 60 percent work within corporate CIO or CTO departments
Read the article .
Liberty seeks common ground with Microsoft on ID
The Liberty Alliance is playing up the promise of cooperation between itself, Microsoft and the open-source OpenID project on identity standards and technologies, but it's being disputed just how much support Liberty's new Concordia Project really has.
Concordia, which officially launched yesterday, seeks common ground between the Liberty specs, which cover scenarios such as identity federation, and user-centric technologies including OpenID and Microsoft's new CardSpace.
Liberty's Conor Cahill, Mike Jones from Microsoft and David Recordon from VeriSign, "representing OpenID", will participate in a panel discussion later this month to discuss with large enterprise users how they will try to make these different technologies work together.
"We'll be brainstorming examples of how various technologies may interoperate with each other or modify themselves in order to interoperate with each other," said Oracle's Roger Sullivan, the president of the Liberty Alliance.
Read the Computer Business Review article
Choosing The Right VPN
by Ian Kilpatrick, director of business development, Wick Hill Group
Summary
- Now a choice between SSL and IPsec VPNs
- Key differentiators between the two
- IPsec - built-in authentication through certificates and the option of different encryption levels. Greater security but more difficult to manage and more costly.
- SSL VPNs - no client software making so more cost-effective and easier to mange. Only one encryption option. Security can be enhanced by incorporating third party authentication.
- SSL strengths and weaknesses
- IPSec Strengths and weaknesses
Other factors in choosing right VPN
- Strength of encryption technology used by both types of VPN
- The type of application
- Sensitivity of the data
- Type of user base
- Location of user base
- Size of user base
- Cost factors
- User access to browsers
- Whether you have multiple sites
- Whether it's a business to business or business/organisation to consumer situation
- Whether IT has access to and control of user devices.
- Which types of applications are suited to which VPN, with examples.
- Future developments
Initially, the only VPN (virtual private network) technology available for securing confidential data in transit between two points was the IPSec VPN standard. In 1999, however, a serious challenger emerged based on SSL (Secure Socket Layer), a capability standard in all browsers.
Read the article
BrandProtect Offers Ten Tips to Avoid Being Targeted by Email Scams
Phishers continue to find ways to circumvent anti-phishing technology as approximately 1.07 percent of all emails contain some form of phishing attack or scam, according to a study issued in January 2007 by MessageLabs. These messages can occur in the form of ‘spoof’ emails that lead consumers to counterfeit Web sites designed to trick them into divulging financial data such as credit card numbers or other sensitive account information, or even chain emails sent illegitimately from a user’s
email to those on their address list. To help protect email account holders from being targeted by these types of email scams, BrandProtect, the industry leader in online brand protection, today announced the top ten ways to avoid having an email account
compromised.
“With the growing complexity of online fraud and brand abuse on the Internet, it has become increasingly difficult for consumers and email account holders to identify fraudulent mail and they are often times subject to attack simply by opening the email,” said Hugh Hyndman, CTO, BrandProtect. “BrandProtect analysts are experts in identifying and taking down online threats and are able to apply this expertise to provide a list of preventative measures to help avoid being a victim of online attacks.”
“Ten Tips to Avoid Email Attacks”
Read the article
Protect Your Ecommerce Customers From Identity Theft
There will be $24.3 billion in online transactions this holiday season; this will undoubtedly be accompanied by an equal rise in the number and type of attacks against the security of online payment systems and against ecommerce consumers. Some of these attacks will utilize vulnerabilities that have become noticeable in the third-party components utilized by websites, such as shopping cart software. Other fraud attempts will most likely use vulnerabilities that are common in any web application and can allow a knowledgeable hacker to penetrate the defenses of an ecommerce host webserver.
There are also the more popular electronic fraud techniques of "spoofing" and "phishing." This activity is on the rise with growing numbers of phishers sharpening their talents, producing quite convincing e-mails and dummy notices from ecommerce web sites; the number of consumers victimized using this method is increasing rapidly. Ecommerce website merchant have a clear mandate to exercise due diligence by doing everything possible to protect their hard-won customers from identity theft.
Read more at ISEdb.com
Web Hosting Watch: Network Security
Hackers are getting smarter; security threats are evolving. So what are the bigger Web hosts doing to protect servers and customer data from third-party Internet villains?
TopHosts.Com spoke to two mega industry players to find out how they view the current state of Web hosting security, and what weapons they hold to combat the delivery of malicious code, spyware and denial of service (DoS) attacks.
Bill Warburton, director of product management for EarthLink Business Solutions, says the job of all Web hosting companies should be to keep pace with hackers and, if possible, to stay one step ahead. While security threats and hacking methods grow in complexity, defense technology and expertise are making strides on the providers' side as well.
Read the TopHosts.com article
Think tank highlights five keys to MiFID compliance
Key hotspots have been identified that financial institutions must address if they are to comply with the forthcoming Markets in Financial Instruments Directive (MiFID).
The hotspots have been pinpointed by 15 leading technology providers who are members of the JWG-IT Technical Special Interest Group (TechSIG) financial industry think tank.
The TechSIG members have allocated resources to three work teams to drill down on what is required of complex infrastructures, applications and data architectures once the directive comes into force this November.
The directive seeks to create a standardised financial services industry operating framework across Europe.
Read the Computer Weekly article
MiFID: CESR's final Level 3 guidelines
The Committee of European Securities Regulators has published its final set of guideline on Level 3 of the Markets in Financial Instruments, clarifying some important issues of the legislation, due to take effect in November.
CESR's final MiFID Level 3 guidance and recommendations, published at the end of last month, cover inducements, best execution, passporting and transaction reporting, and focus on the operational aspects that arise as a consequence of the provisions of the Directive and its implementing measures, and on “identifying practical solutions to address the regulatory challenges to ensure certainty amongst market participants”.
The recommendations go a long way to removing some of the uncertainties that remain for firms implementing MiFID. Alan Jenkins, European head of MiFID at BearingPoint, welcomed the recommendations on transaction reporting, saying that they could just about be characterised as a breakthrough” and were “remarkably liberal”. In other areas, he said that the there was now “good clarity”, though it was not all that investment firms could have hoped for.
Read the article in Banking Technology
FSA withdraws IDD and Menu from MiFID plans
The FSA has withdrawn plans to include Initial Disclosure Documents and the ‘Menu' on top of the information requirements for the Market in Financial Instruments Directive.
In January the FSA submitted a notice to the European Commission stating its intention to retain the rules concerning IDDs and the Menu which meant its regulations would go beyond the provisions of MiFID.
Following this decision the FSA commissioned research by CRA International to investigate the benefits of the Menu, however the results found only limited evidence that the ‘Menu' has reduced provider bias in advice sales.
Read the article in IFAOnline
UK Getting tough on Computer Misuse
Computer misuse takes many forms including hacking of certain types of computer, fraud, denial of service attacks and the spreading of viruses, worms, trojan horses, time bombs and other malicious code. Hackers and other ‘computer terrorists’ have the potential to cause serious disruption to organisations, businesses and individuals. It is estimated that each year in the UK computer misuse costs between £400 million and £2 billion in damage caused to computer systems.
Computer misuse has traditionally been covered by the Computer Misuse Act 1990 (CMA) which sets out two key offences:
- unauthorised access to computer programs or data (i.e. hacking), together with a more serious version of the offence if the hacking is carried out with an intent to commit or facilitate further offences; and
- unauthorised modification of computer material.
However, the Police and Justice Act 2006 (PJA) introduces long-awaited amendments to the CMA aimed at bringing it up to date with the latest developments in computer crime and imposing tougher penalties. These amendments are likely to come into force in the next few months.
Read the article
Data misuse threat to trust in police IT
Potential security breaches by police insiders risk undermining public confidence in law-enforcement surveillance technologies, such as the number plate recognition system and fingerprint database , the former head of police IT has warned.
Phillip Webb, who stepped down as chief executive of the Police IT Organisation in March, said that the potential for insiders or others to misuse information held on police databases could undermine public support for the technology and the laws that allow its use.
Speaking on the growth of electronic surveillance at the Government IT Summit , Webb said that technologies such as automatic number plate recognition systems and electronic fingerprint records were "marvellous tools" that could protect society from dangerous people.
But he said it was essential that information is "applied correctly, is used correctly and is not misused".
Webb said he was concerned, in particular, that insiders and others could misuse the automatic number plate recognition system, which is the largest Oracle database in Europe. He said, for example, that it could be used to track the movements of celebrities or politicians.
Read the Computer Weekly article
Verisign plugin brings green address bars to Firefox
Verisign Inc. has brought a new technology, used to identify trusted Web sites, to the Firefox browser.
The Internet services vendor has released a Firefox plugin that will show the same type of green address bar that is displayed by Internet Explorer 7 when it lands on certain highly trusted Web sites that use Extended Validation Secure Sockets Layer (EV SSL) certificates.
Companies such as Verisign, Entrust Inc., and Network Solutions LLC have been issuing these certificates since late 2006, but browser makers have been slower to adopt them. They were adopted by Internet Explorer 7 in late January, and Firefox is expected to support the certificates in Firefox 3.0, expected late this year.
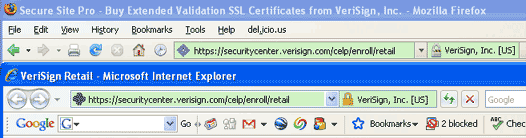
Read the NetworkWorld article
Summary
- Recent growth of SSL VPNs
- Aim of VPN technology - controlled, secure and managed access to any application, from any device and from any location.
- Integrated authentication
- Inclusion of client integrity
- Fewer security issues with SSL
- SSL VPNs advantages
- SSL VPN disadvantages
- Cost considerations and benefits
- How do you choose a VPN?
The growth of Secure Sockets Layer virtual private networks (SSL VPNs) has accelerated in the last 12 months due to greater awareness among users of the commercial advantages, better marketing which focuses on benefits rather than technology, and improved security features.
The ultimate goal of SSL VPN technology is to allow controlled, secure and managed access to any application, from any device and from any location. Early implementations had some limitations such as user account information not being cleared down from the browser after user sessions, no support for dynamic port assignment, support only for web-enabled applications, and no strong authentication of the user or the access device.
All of these, and other concerns, have been addressed as SSL technology has matured. Recent enhancements, for example, include the integration of user authentication. Many SSL VPN vendors offer, or are planning to offer, integrated third party strong authentication products such as those from VASCO and RSA. Netilla, from AEP Networks, and FirePass, from F5, both natively embed VASCO user authentication with their SSL VPN offerings
read the article
MiFID - FSA confirms Industry Guidance on outsourcing
The Financial Services Authority (FSA) today (16 May 2007) confirmed that its supervision of outsourcing by firms will in future take account of industry guidance which has been issued by MiFID Connect.
This is the first guidance developed by industry which the FSA has recognised since publishing its Discussion Paper 'FSA confirmation of Industry Guidance' in November 2006, and the first formal Industry Guidance related to the Markets in Financial Instruments Directive. The guidance covers so-called 'common platform' FSA firms - those subject to MiFID and/or the Capital Requirements Directive. MiFID Connect is a joint project set up by 11 trade associations to support their members in implementing the Directive.
The Discussion Paper set out plans to encourage greater use of Industry Guidance as the FSA moves toward a more principles-based approach to regulation.
Read the article
Roche Diagnostics – Anatomy of a serious data breach
On Wednesday 9 May 2007, the Roche Diagnostics marketing team must have been very happy. The very first edition of ‘Reach' had been sent to all the people who had registered for the Accu-Chek newsletter. Accu-Chek is a range of diabetic monitoring equipment for the patient's own use, and is well known and well respected, as is Roche Diagnostics. But, as the newsletter hit inboxes, they learned that things had gone very wrong indeed, and that highly confidential medical data about patients was haemorrhaging from their database.
Read the article
Seven Tips for Selecting UTM Appliances
By Ian Kilpatrick, Chairman Wick Hill Group
Read Ian's UTM Selection tips
UK Information Commissioner prosecution
The UK Information Commissioner recently took another step forward in his campaign to halt the unlawful trade in personal information.
A press release issued at the end of April confirms that a private investigation firm, Infofind Limited, has pleaded guilty to illegally obtaining personal data from the Department for Work and Pensions ("DWP") on behalf of a finance organisation. The offence involved individuals purporting to be employees of the DWP and by doing so, deceiving other DWP staff members to disclose data. s.55 of the Data Protection Act 1998 ("DPA") provides that it is an offence to unlawfully obtain, disclose or sell personal information, without the consent of the data controller.
Read the article, Courtesy of Eversheds
UK Information Commissioner audits HBOS
The Information Commissioner's Office (ICO) is conducting an audit of Halifax Bank of Scotland (HBOS)'s data security procedures after it was revealed that the bank was putting customers' financial documents in ordinary bins.
The act, uncovered by the BBC's Watchdog programme, is in breach of an undertaking to the ICO signed by HBOS earlier this year after it was found throwing out documents containing customer details.
The ICO is conducting an audit of HBOS and its security procedures and will soon examine the evidence gathered by Watchdog. If a breach is found then it will serve an enforcement notice on the bank. A repeat offence in breach of the notice will be a criminal offence and will open HBOS to prosecution.
Read the OUT-LAW.com article
UTMs Can Simplify Security Systems Management And Cut Costs
Ian Kilpatrick, chairman of Wick Hill Group, looks at how UTMs help with security systems management and advises on choosing a UTM appliance.
Summary:
- UTMs becoming much more popular. They reduce costs and simplify security management
- UTM definition
- Used mainly by SMEs. Also now by larger organisations
- UTMs pros and cons
- UTMs provide easier hardware and software management
- What to look for when buying UTMs.
Unified threat management systems (UTMs) have been growing in popularity for the last few years. This is largely because they provide an excellent means of reducing security costs and simplifying the whole process of security systems management and installation. UTM growth is predicted by many analysts to significantly exceed that of firewalls and individual point security solutions over the next few years.
Read the article
Smart Card Alliance Leads Education Effort on Identity Management
With reports of security breaches increasingly in the news, commercial and government organisations recognising the critical need to strengthen IT security are often turning to cards, tokens and new software solutions. The Smart Card Alliance will lead the discussion on these and other trends in cybersecurity and identity management in its full-day educational session, May 16th from 8:30am to 4:30pm at the SecurTech 2007 conference on secure identification, part of CardTech/SecurTech (CTST) 2007.
"Trusted and secure digital identities are a top priority for government and commercial organisations, but how to get there isn't always clear," said Randy Vanderhoof, executive director of the Smart Card Alliance. "In this session, speakers from top solution provider and user organisations will explore how it is done and in use today–from available technology, to issuance and management of credentials, to real life implementations. It is a must-attend for IT professionals."
Read the article in SDA India
Managers’ lax e-mail use is ‘putting security at risk’
Managers are jeopardising the security of company information by exchanging unsecured, confidential information in e-mail sent to shared inboxes.
According to a survey of 300 PAs at 250 companies by e-mail management firm Mesmo, this results in 82% of them reading confidential information in error.
The research examined who controls the e-mail inbox in the PA/manager relationship and how managers behave as e-mail users.
Although many executives manage their own e-mail - often by remote devices such as Blackberries - most hand over their inboxes to their PA when they are out of the office or in meetings.
Read the Computer Weekly article
eBay expands PayPal buyer protection scheme
eBay Australia has put its payment scheme PayPal at the centre of its buyer protection initiatives, doubling the amount it will pay back to customers for dodgy transactions involving a PayPal payment and extending the scheme to low-value transactions and new sellers. At the same time, the auction company's eBay-branded protection scheme will be phased out.
From June 7, eBay will refund up to $3,000 if a buyer pays for goods using PayPal and becomes involved in a disputed transaction. Previously, the limit was $1,500. Typical causes of disputes include failure to deliver any goods at all, or items differing hugely from their online description.
Sellers only qualify for the full protection scheme if they have more than 50 feedback messages and a 98% positive reputation. However, transactions with sellers falling under those thresholds will still be covered for up to $400, including postage costs.
The lower value scheme will replace eBay's existing buyer protection scheme, which included a $25 administration fee, making it useless for smaller purchases. It also establishes PayPal as the only means of payment with any form of eBay-backed guarantee. "The company will no longer be providing coverage when a person pays through other means," eBay trust and security director Alastair MacGibbon told iTWire
Read the ITWire article
RBS to issue online banking customers with smartcard readers
Royal Bank of Scotland is the latest bank to issue card readers to its online banking customers to help prevent fraud.
Barclays announced a similar move last month. Royal Bank of Scotland has signed a contract with XIRING to supply the readers, and first customers are receiving their personal readers this week.
Read the Computer Weekly article
RSA Broadens Reach of RSA SecurID ® Two-Factor Authentication Solution with Expanded Support for Leading Mobile Device Platforms
RSA SecurID ® Software Tokens now support Java™ Micro Edition Platform and will support Windows Mobile ® platforms, enabling secure access to enterprise resources from mobile devices
RSA SecurID ® two-factor authentication technology now supports the Java™ Platform, Micro Edition (Java ME platform) and will soon support Windows Mobile ® platforms. Smart phones based on these platforms can now be provisioned with a RSA SecurID Software Token, eliminating the need to carry a separate RSA SecurID hardware authenticator .
A mobile device with an RSA SecurID Software Token activated is engineered to provide a convenient mechanism for securely accessing network resources, while bringing confidence, flexibility and choice in strong authentication to consumers and enterprises.
RSA SecurID Software Tokens are now designed to support devices built on the Java ME platform - such as the Nokia Eseries family of business optimized devices powered by Symbian OS 9 with Platform Security and S60 3rd Edition with Java ME platform. With support for the Java ME platform, users can now leverage RSA SecurID software authenticator technology on a brand new class of everyday devices. In addition, RSA SecurID Software Tokens are engineered to now support the latest Windows Mobile 5.0 and 6.0 platforms, utilized by devices such as the soon-to-be-launched Motorola MOTO Q 9h smart phone and handsets available from major mobile service providers.
For years, RSA SecurID Software Tokens have been supported on other leading mobile devices including Microsoft ® Pocket PC, Palm ® Treo™ smartphone, and RIM ® BlackBerry ® devices. With new support for Java ME platform and Windows Mobile platform, RSA now provides two-factor authentication functionality for the majority of mobile platforms available on the market today. Certain devices, such as the high performance MOTO Q 9h smart phone, are also designed to provide integration between the embedded RSA SecurID Software Token technology and the device's VPN client to seamlessly enable two-factor authentication for remote access, creating an easy-to-use, secure corporate network access experience for today's on-the-go professional.
Read the article
Hacking contests bad for business - Gartner
A pair of Gartner analysts Tuesday denounced a recent hack challenge that uncovered a still-unpatched QuickTime bug, calling it "a risky endeavor" and urging sponsors to reconsider such public contests.
The research manager of TippingPoint, the company that paid $10,000 for the QuickTime vulnerability and its associated exploit, rebutted by saying that at no time was there any danger of the vulnerability escaping from responsible parties.
Dino Dai Zovi was the first to hack a MacBook Pro at CanSecWest, a Vancouver security conference held two weeks ago. For his trouble, Dai Zovi took home the $10,000 prize offered by TippingPoint's Zero Day Initiative, a bug bounty program that's been in operation nearly two years.
Security researchers have called the QuickTime bug, which can be exploited through any Java-enabled browser, "very serious." Apple has yet to patch -- or announce when it will patch, the vulnerability.
"Public vulnerability research and 'hacking contests' are risky endeavors and can run contrary to responsible disclosure practices, whereby vendors are given an opportunity to develop patches or remediation before any public announcements," said analysts Rich Mogull and Greg Young in a research note published by Gartner on Monday.
Read the ComputerWorld Singapore article
VeriSign and Innovative Card Technologies Address Worries of Online Merchants with New Fraud Protection that Fits in a Wallet
VeriSign Identity Protection Integrated with ICT DisplayCard to Generate Unique New Password for Every Transaction, Adding Convenient New Way to Access Growing Authentication Network
VeriSign, Inc. (NASDAQ: VRSN), the leading provider of digital infrastructure for the networked world, and Innovative Card Technologies, Inc. (NASDAQ: INVC), developers of the ICT DisplayCard for e-banking, e-commerce and data access authentication, today announced an agreement that will make it easier than ever for financial services providers and retailers to issue and accept payment cards embedded with one-time-password (OTP) authentication to protect their online transactions from e-fraud.
Now companies that fortify their online commerce applications with VeriSign Identity Protection (VIP) can leverage the ICT DisplayCard, a revolutionary new “smarter” payment card with built-in identity authentication. The ICT DisplayCard integrates the security of a one-time password token into a card the size of a standard credit or debit card. At the push of a button on the back of the card, an integrated display shows a password that changes with every transaction. During an online transaction, this number is entered into a user interface with other information (such as the user's static PIN and login name) for multifactor authentication.
Read the article
PayPal security measures help stamp out fraud
PayPal's 133 million online customers are the biggest ocean phishers have to plunder. CISO Michael Barrett wants to make it safe to be in the water; and he's not going at it alone. Backed by PayPal's sophisticated fraud models and help from ISPs and browser makers, Barrett is succeeding in protecting the most-spoofed brand on the Internet.
Can you quantify losses due to phishing for PayPal?
Michael Barrett: Forty-one basis points is the total fraud number [on PayPal's fraud model], and we don't break out where phishing is in that overall mix. I will say: it isn't very high on that list. That's one of the issues here; there is a perception there is a huge problem, whereas the financials don't indicate that. Part of the issue is there's been a certain amount of hype about the magnitude of the problem from a financial sense. I don't at all discount the perception impact, but I don't think the financial impact is what some elements are saying it is.
How does PayPal defend against phishing?
Barrett: One of the back-end defenses we have is a lot of fraud modeling. It's very advanced, and it's resulted in extremely low fraud rates compared to the rest of the financial services industry. We've gotten very good detecting fraud on the back end, so what's [the phishers'] response? They generate more mail on the front end.
Read the full interview at Search Security.com
‘Give me more power,' says UK Information Commissioner
The information commissioner has proposed new safeguards to ensure the UK does not become a “surveillance society”.
Giving evidence before the Home Affairs select committee, information commissioner Richard Thomas has also called for stronger powers to allow his office (the ICO) to carry out inspections and audits.
Currently, the commissioner must gain consent before inspecting an organisation for compliance with the Data Protection Act.
Thomas said, “People now understand that data protection is an essential barrier to excessive surveillance. But it is wrong that my office cannot find out what is happening in practice without the consent of each organisation.”
There is also a concern that too much surveillance will create a climate of fear and suspicion, said Thomas.
Read on in Computer Weekly