VeriSign Security Review - May 2006
As phishing continues to mature, one of the last sanctities supposedly free of such malice has been under attack. The SSL/TLS encrypted Web page used for securely transmitting private information has seen increased abuse by phishers. They took advantage of loopholes in some SSL Certificate practices and obtained certificates that make them look legitimate.IE 7 will change that, and enterprise security managers should take notice: the advent of High Assurance Certificates will prove its long-term effectiveness against phishing.
In this issue:
Hot Topics
Standards and Regulations
News from VeriSign
Security Events
MetaFisher – The New Face of Botnets
Three The last two years saw the emergence of Web-controlled botnets used for attacks such as phishing, and MetaFisher was the most sophisticated such botnet.
MetaFisher appeared in 2005 as a Bot and security analysts knew immediately that it was a highly sophisticated work in progress. In late 2005, at the height of the Microsoft Windows Media File (WMF) incident, MetaFisher activity ramped up. In February 2006, when VeriSign iDefense Labs spotted MetaFisher's unusual encrypted communication with a Web site, it investigated further and discovered that a sophisticated command-and-control center via a PHP interface was used to manage a bot family and trigger phishing attacks. MetaFisher managed to evade anti-virus and intrusion detection systems by running as a browser help object (BHO) on the infected computer.
In March, VeriSign iDefense Labs broke the encryption scheme used to control MetaFisher infected computers and, through painstaking analysis and cooperation with other researchers such as Sunbelt Software and Symantec, correlated the codes and scope of the attacks to date which included banks in the U.K., Germany, and Spain. The VeriSign iDefense team then worked with VeriSign's Security Operations Center (SOC) to develop and deploy snort signatures to effectively detect MetaFisher activities.
VeriSign leveraged its intelligent infrastructure services supported by a team of analysts and engineers to best understand the full scope of this massive and sophisticated operation. VeriSign also had the customer reach to prevent devastating attacks on financial targets.
Back to Top
April Threat Summary
The VeriSign iDefense Threat Level eased after patches came out for the Microsoft 06-012 vulnerability. Microsoft, however, has just released two new critical bulletins, Microsoft 06-019 involving Microsoft Exchange, and Microsoft 06-020 involving Macromedia Flash in Windows XP and IE 6. Both could allow remote code execution.
Cloudmark detected two phishing schemes that used Voice over IP (VoIP) to collect personal banking information. Phishers may have been using this technique for some time, though these are the first detected attacks of their kind. More at Information Week.
Sendmail, Inc. reported a race condition vulnerability that affects the mail transfer agent on a wide scale. A remote, unauthenticated attacker could execute arbitrary code with the privileges of the Sendmail process. If Sendmail is running as root, the attacker could take complete control of an affected system. Sendmail has provided an Advisory and a new version of the software is available.
On April 18, Oracle Corporation released a security bulletin that addressed 39 vulnerabilities in multiple products. The security bulletin did not release details on those vulnerabilities.
Back to Top
IE 7 Beta 2 Released
Microsoft has released an updated test version of IE 7 for Windows XP and is hoping to convince the public to try out the evolving software. To help spur downloads of IE 7 Beta 2, the company is offering free telephone support for customers in Germany, Japan, and North America.
Asia Now #1 Spammer
Asia has overtaken North America as the top spam relaying region in the world, according to a report released on Thursday by Sophos. According to the report, nearly one half the spam worldwide originated in Asia. North America was a distant second with just over 25 percent. On a per-country basis, the U.S. remains Number One while China is a close second. Read more .
Authorize.net Hacked
Online payment service provider Authorize.net reported on April 3 that its online processing service had been used by hackers attempting to steal money from credit and debit cards. The hackers ran 3,000 transactions on stolen credit cards over one weekend, but the theft was foiled when the Authorize.net auto-generated email alerted merchants of the processed payments. All fraudulent charges were voided.
Back to Top
Standards and Regulations
GAO Reports On SOX Burden
The Government Accountability Office (GAO) is releasing a report confirming that smaller firms indeed carry a proportionally heavier financial burden on Sarbanes-Oxley compliance. The SEC needs to come up with new regulations aimed at reducing smaller firms' compliance cost, the report says. It does point out that a lot of the cost is due to confusion and one-time startup costs.
First Local WiFi Security Law
Concerned with identity theft and other crimes over the wireless networks, New York's Westchester Country enacted a law that requires businesses to install basic security measures when customers' personal information is transmitted via wireless networks. Read more .
Back to Top
News from VeriSign
VeriSign Hosts Risk Management Talks
With a keen understanding of customers' needs to balance security investments with security risks, VeriSign is inviting IT professionals to a series of risk management talks. In this six-city tour through New York, Washington, D.C., Atlanta, Chicago, Dallas, and Mountain View, IT professionals will have a chance to mingle with each other and hear discussions on the holistic view of threats, vulnerabilities, network access policies, and potential business impacts in assessing security risk. VeriSign will demonstrate how to dynamically generate a risk score including financial impacts, to simulate and model the effects of changes, and to measure compliance with both internal and external policies and regulations.
Back to Top
Get Ready for IE 7
High Assurance SSL: What Does It Mean To You?
Many enterprise customers have asked about the upcoming Microsoft IE 7 release and what it would mean to enterprise security. VeriSign is engaged in one of the most significant developments in IE 7: the new High Assurance SSL Certificates for securing online transactions.
With the new IE 7 release, there will be a new kind of SSL Certificate to assure users of the identity of an encrypted site. Whereas other certificates will retain the same cumbersome user interface as they have in Internet Explorer 6, High Assurance certificates display the organizational identification and the issuing certificate authority (CA) right in the top address bar and also turn the address bar green to signal safety.
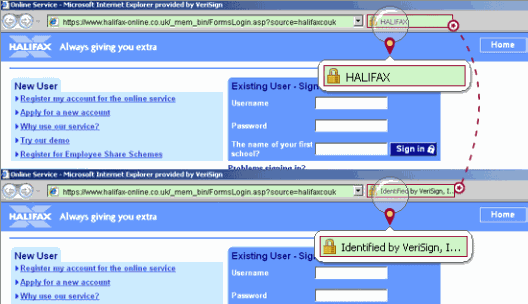
To issue a High Assurance certificate, the CA must validate the applicant organization through vetting processes that meet the High Assurance standard. To meet the High Assurance standard, a CA may have to bolster its certificate issuance practices. Issuing a certificate merely upon verifying the domain name ownership, for example, does not meet the High Assurance standard and can not be displayed as such.
Back to Top
What Should You Do to Get Ready?
As IE 7 gets wider market adoption, site visitors will likely be looking for High Assurance when they consider giving up personal information. For large enterprises, High Assurance certificates will not only bolster customer confidence, but in the long run, it will also become one of the most effective anti-phishing tools, as they are nearly impossible to spoof.
Prepare to meet your customers' demand for IE 7 and High Assurance SSL by talking to your certificate authority (CA). You may be going through a more stringent vetting process than before. Your IT manager in charge of certificate issuance, for example, may need further proof that he or she indeed has the authority to do so. Other administrative steps to ensure a smooth transition include making sure that your registered domain names are correctly listed and have the right contact names. VeriSign has been a leading contributor to the emerging High Assurance SSL standard. Contact your VeriSign representative for more information.
Back to Top
Security Events
May 23-25, 2006
World Enterprise Information World
Secaucus, NJ
June 4-6, 2006
GLOBALCOMM 2006
Chicago, IL
June 5-7, 2006
Gartner IT Security Summit
Washington, D.C.
June 6-7, 2006
NACHA Authentication Mandate
Reston, VA
June 27-29, 2006
Identity Management Conference
Chicago, IL
Back to Top