'Enhancing PKI Security – Outsourcing vs. In-House Deployments'
By Andrew Horbury, VeriSign UK Marketing Manage
[Also Read: "Double lasts longer" | "Improving Confidence in Online Security"]
The eSecurity Evolution
The Internet's rapid growth, accompanied by an increase in security attacks globally, has meant the requirements for eSecurity are continually evolving. Firewalls, virtual private networks (VPN), anti-virus, and public key infrastructure (PKI) are now critical components of any strong security policy.
Consumers are also placing increased importance on eSecurity, and many view this as a key component to building trust with the vendors they wish to do business. At the same time, European governments have stepped up finalising legislation around the protection of privacy and the legal recognition of electronic signatures.
All these dynamics are raising the fundamental awareness of eSecurity, and the importance of high security, of which PKI plays a critical role. PKI is now considered a basic enabler of new eBusiness revenue streams, and has crossed the boundaries of security over the years. It has enabled a host of new services which were not acceptable for the Internet in the past due to the lack of enhanced security, for example:
• Digital Signing of electronic documents
• Electronic supply chain management
• Electronic (e)Ordering & eProcurement
• Online eGovernment Services
Today, the challenge for many organisations is how to bridge the gap from their current IT infrastructure, to enhanced security using PKI. The decision organisations need to make is whether to invest in a PKI solution in-house or outsource it to a trusted third party provider. Both approaches are intrinsically different and offer organisations a unique value proposition.
The challenge for IT decision makers is to weigh the pros and cons of each approach, and determine which model is best suited to continually deliver the highest level of security to their organisation.
Setting the Stage - Outsourced vs. In-house PKI
PKI is one of the few technologies integrating Legal Practices & Information Technology disciplines. This results in several unique challenges in deployment, but is also a reflection of the distinctive nature that PKI serves the Internet, namely:
• identifying the existence of a company, and recognising individuals through the use of digital certificates, and
• binding digital signatures to the same legal validity as a hand written signature.
To overcome the legal and technological obstacles, implementing a PKI solution has resulted in two fundamentally different approaches referred to as in-house PKI and outsourced PKI solutions, both offering unique value propositions .
In-house PKI
In-house PKI involves the implementation of a managed in-house PKI solution. A company purchases PKI software and hardware which is used to deploy digital certificates to individuals. Dedicated staff are responsible for defining their own certificate practices and policies for the creation and distribution of digital certificates throughout the corporate infrastructure. Companies perceive that this approach offers inherent ownership and flexibility, but typically this option requires a large upfront investment in both time and money.
Outsourced PKI
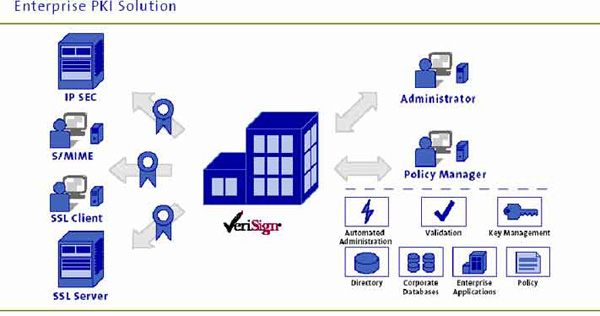
Outsourced PKI is analogous to the service provider market whereby the ownership of infrastructure is with an external entity known as a Certificate Authority (CA). The CA is responsible for setting policy, managing information technology (IT), and owning liability ownership on behalf of the customer. The advantage to the customer is control of their certificate issuance, co-branding, and management, while moving the responsibility of maintenance, scalability, and policy management to the back-end (commonly referred to as the processing centre).
Furthermore, outsourced solutions cover all aspects of the PKI infrastructure, including:
• Legal : Certificate Policy Statement (CPS) and Certificate Practices (CP) establish the legal framework of PKI
• Technical : The CA maintains the ability to migrate PKI to new standards and technological upgrades
• Human Resources: Project management, policy management, and certificate deployment costs are off-loaded to the CA
Weighing the Pros and Cons in Order to Get it Right
The decisions around eSecurity spending are often compared to the metrics of low cost, flexibility, control, and speed of deployment. In-house deployments are sold on the perceived merits of greater control, flexibility and lower costs in the long term. In house certificates are expected to be issued and revoked quickly, and security policies tailored to business needs.
On the other hand, allowing companies to outsource their security gives them more flexibility to concentrate on their core business, and results in lower cost when the total cost of ownership is taken into account.
The trade-off is often judged on "up front costs", since companies will often compare their in-house proposal cost to that of an out-sourced vendor. But businesses should avoid getting caught up in the shadow of proposal costs, ignoring tangible factors such as Total Cost of ownership (TCO), and investment protection of a given solution.
Consider the following example. For certificate services, businesses typically need to take the following total deployment costs into consideration:
• Human Resources : Project management and operational and maintenance support costs
• Infrastructure : Hardware and software costs which form the basis of the PKI infrastructure
• Services : Training costs, external consultant services, and security audits
• Legal and policy requirements
In the case of an in-house PKI solution, all the services, HR, infrastructure and legal components are the responsibility of the organisation hosting the PKI solution.
On the other hand, in the typical outsourced PKI model, the organisation will incur a much smaller investment in HR, consultancy, and infrastructure since the bulk of the investment lies in the CA Infrastructure. The ownership of a carrier class processing facility, operations, and maintenance, and the legal framework also become the responsibility of the CA.
Organisations looking to invest in an in-house PKI model must also consider several other factors to ensure they adhere to the highest level of security.
• Take Responsibility for Security: Organisations need to manage their own root key, private keys of deployed certificates, and audit logs
• Ensure that a common standard is being enforced: Organisations must set their own policies and practices. Yet its only when two companies utilise the same standards of PKI that they can inherently trust each other
• Determine policy: Organisations need to determine, document and implement their own policy, and take the responsibility (and risk) of certificate issuance and authentication
• Continually invest in the PKI solution: Organisations must be prepared to make investments in hardware upgrades as more users are added, and software upgrades as new standards are implemented.
For organisations considering the outsourcing model , the benefits are summarised as follows:
• Organisations can focus on their core business
• No hardware and software investment is required for PKI infrastructure
• TCO is reduced
• Third party is liable for security
• CA is responsible for technology changes
• Enable trust with other companies through common PKI standard
What's the Market Demanding?
So how has the market responded recently to PKI? Several analyst reports are showing a trend towards the outsourced PKI model. According to Datamonitor, estimated revenues for outsourced vs. in-house PKI deployments are going to reach 53% against 42% this year. Datamonitor also predicts further growth in outsourced PKI market share, and expects it to reach 60% share by 2006.
It appears outsourcing is becoming increasingly attractive as it removes the burden of a large upfront investment, and takes the emphasis off licensing as the main revenue stream. This has become even more important during times of economic difficulty, as cost-cutting becomes a primary concern.
But regardless of whether organisations choose to outsource or deploy a PKI solution in-house, taking advantage of PKI to deliver enhanced levels of security will require a strong commitment, and solid security policies.
Into the future
The inability to share data over a network without an increased security risk limits the ability of organizations to conduct business in the most efficient way, and the lack of a viable single sign-on framework is inhibiting the growth of electronic commerce and networked operations. Launched at the 2004 RSA conference in San Francisco the Initiative for Open Authentication (OATH) addresses these challenges with standard, open technology that is available to all. OATH is taking an all-encompassing approach, delivering solutions that allow for strong authentication of all users on all devices, across all networks.
OATH's vision is of the network of the future where consumers feel secure entering personal information online, where business partners can safely collaborate and share data across domains, and where devices constitute secure threads in a tightly-woven network fabric. Open Authentication reference architecture (OATH), a revolutionary approach designed to accelerate the adoption of strong authentication technology across all networks. Leveraging existing standards and an open reference platform, OATH will ensure that secure user and device credentials can be provisioned and verified by a wide variety of industry-leading software and hardware solutions, removing traditional barriers to widespread adoption.
OATH is comprised of industry leaders working with other standards groups toward the propagation of ubiquitous strong authentication, enabling eBusiness and giving customers the confidence to conduct secure commerce and communication online. An OATH ecosystem consists of devices, chip sets, platforms, applications, integrators, and customers, all working together in a strongly authenticated, highly secure environment
For more information about OATH, please visit www.openauthentication.org
[Also Read: "Double lasts longer" | Back to "Improving Confidence in Online Security"]
[Also Read: "Double lasts longer" | Back to "Improving Confidence in Online Security"]